
Achieve a Data-Centric Approach to Zero Trust with NetApp ONTAP

Daniel Tulledge
The old model: Trust but verify. The new model: Verify and never trust.
Data is the most important asset your organization has. Insider threats are the cause of 28% of data breaches, up 14% from the previous year, according to the 2018 Verizon Data Breach Investigations Report. Insiders Chelsea (formerly Bradley) Manning and Edward Snowden leaked classified data, but they didn’t need to have access to that data to perform their jobs. So, who should be trusted? Nobody. Organizations need to ramp up their vigilance to DEFCON 1—but how? By deploying a Zero Trust implementation around your data. NetApp® ONTAP® data management software has industry-leading capabilities to deploy Zero Trust controls.
What Is Zero Trust?
The Zero Trust model was originated by John Kindervag at Forrester Research. Its intent is to design network security from the inside-out rather than the old outside-in notion. The inside-out Zero Trust approach involves determining a microcore and perimeter (MCAP). The MCAP is an interior definition of data, services, applications, or assets to be protected by a comprehensive set of controls. The concept of a secure outer perimeter is obsolete. Entities that are trusted and allowed to successfully authenticate through the perimeter can then make the organization vulnerable to attacks. Insiders, by definition, are already inside the secure perimeter. Employees, contractors, and partners are insiders, and they must be enabled to operate with appropriate controls for performing their roles within your organization’s infrastructure.
Achieving a Data-Centric Approach to Zero Trust with ONTAP
To build a Zero Trust network, you can apply a data-centric approach. The security controls should be as close to the data as possible. The capabilities of NetApp ONTAP, coupled with the NetApp FPolicy™ partner ecosystem, can provide the necessary controls for the data-centric Zero Trust model. ONTAP is NetApp’s security-rich data management software, and FPolicy is an industry-leading ONTAP capability that provides a granular file-based event notification interface. NetApp FPolicy partners can use this interface to provide greater illumination of data access within ONTAP.
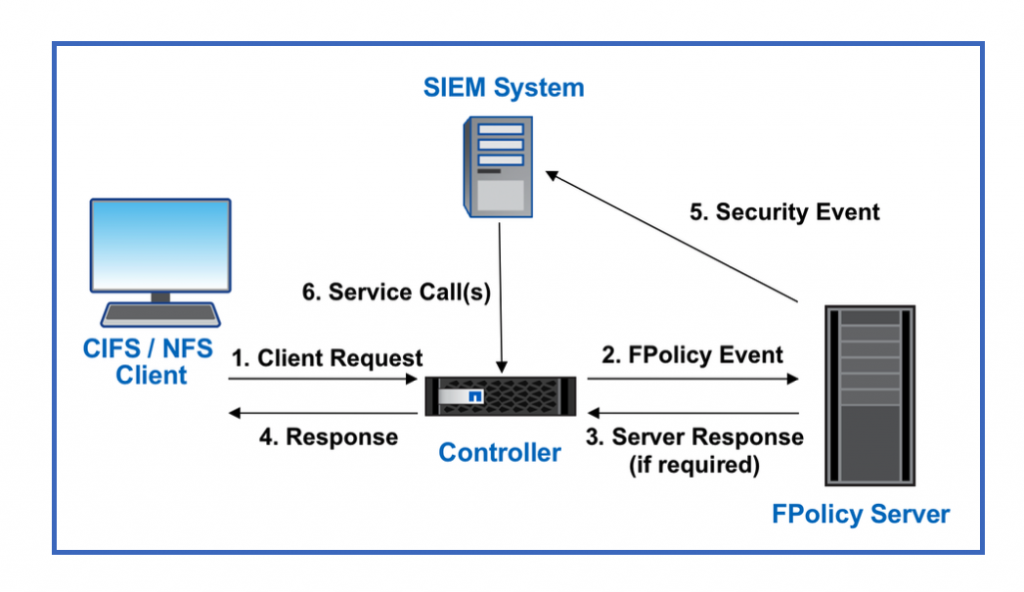 FPolicy Architecture[/caption]
FPolicy Architecture[/caption]
To architect a zero trust data-centric MCAP, follow these steps:
- Know where your organization’s data is.
- Classify your data.
- Securely dispose of data you no longer require.
- Understand what roles should have access to the data classifications.
- Apply the principle of least privilege to enforce access controls to verify and never trust.
- Use multifactor authentication for administrative access and data access.
- Use encryption for data at rest and data in flight.
- Monitor and log all access.
- Alert suspicious access or behaviors.
Where Is Your Data?
The FPolicy capability of ONTAP, coupled with the NetApp Alliance Partner ecosystem of FPolicy partners, lets you identify where your organization’s data exists and who has access to it. This is done with user behavioral analytics (UBA), which identifies whether data access patterns are valid; I’ll discuss it in more detail later. If you do not understand where your data is and who has access to it, UBA can provide a baseline to build classification and policy from empirical observations.
Classifying Your Data
Classification of the data, in the terminology of the Zero Trust model, involves identification of toxic data. Toxic data is sensitive data that is not intended to be exposed outside an organization. Disclosure of toxic data is likely to result in violation of regulatory compliance and might result in damage to an organization’s reputation. In terms of regulatory compliance, toxic data maps to cardholder data for the Payment Card Industry Data Security Standard (PCI-DSS), personal data for the EU General Data Protection Regulation (GDPR), or healthcare data for the Health Insurance Portability and Accountability Act (HIPAA). You can quickly see the value of a data-centric Zero Trust architecture as a framework for meeting an organization’s compliance requirements.
Delete the Data You No Longer Require
After classifying your organization’s data, you will discover that some of your data is no longer necessary or relevant to the function of your organization. Unnecessary data is a liability to retain. It should be deleted.
Controlling Access to Your Data
Mapping access to the sensitive data and applying the principle of least privilege means giving people in your organization access only to the data required to perform their jobs and nothing more. This involves the use of role-based access control (RBAC), which applies not only to data access but also administrative access. With ONTAP, an SVM can be used to segment organizational data access by tenants within an ONTAP cluster. RBAC can be applied to data access as well as administrative access to the SVM. RBAC can also be applied at the cluster administrative level.
Multifactor Authentication
In addition to cluster administrative RBAC, multifactor authentication (MFA) can be deployed for ONTAP web administrative access and Secure Shell (SSH) command-line access. MFA for administrative access is a requirement for U.S. public sector organizations or those that must follow the PCI-DSS. Administrative web access to NetApp OnCommand® System Manager or OnCommand Unified Manager is enabled by Security Assertion Markup Language (SAML) 2.0. SSH command-line access uses chained two-factor authentication using a public key and password.
Data-at-Rest Encryption
Each day, there are new requirements for mitigating storage system risks and infrastructure gaps when an organization repurposes drives, returns defective drives, or upgrades to larger drives by selling or trading them in. As administrators and operators of data, storage engineers are expected to manage and maintain data securely throughout its lifecycle. NetApp Storage Encryption (NSE) and NetApp Volume Encryption (NVE) offer options for solving the challenge of making sure that all your data at rest is encrypted all the time, whether or not it is toxic, and without affecting daily operations. NSE is an ONTAP hardware data-at-rest solution that makes use of FIPS 140-2 level 2 validated self-encrypting drives. NVE is an ONTAP software data-at-rest solution that makes use of the FIPS 140-2 level 1 validated NetApp Cryptographic Module. With NVE, either hard drives or solid-state drives can be used for data-at-rest encryption. Plus, NSE drives can be used to provide two layers of encryption. NVE also provides a capability called secure purge to cryptographically remove toxic data. Either the Onboard Key Manager (OKM), which is the key manager built in to ONTAP, or approved third-party external key managers can be used with NSE and NVE to securely store keying material.
Data-in-Flight Encryption
ONTAP data-in-flight encryption protects user data access and control plane access. User data access can be encrypted by SMB Encryption for Microsoft share access or by krb5P for NFS Kerberos 5. Control plane access is encrypted with Transport Layer Security (TLS). ONTAP provides FIPS mode for control plane access, which enables FIPS-approved algorithms and disables algorithms that are not FIPS approved.
Monitoring and Logging Data Access and Suspicious Behavior
After RBAC policies are in place, active monitoring, auditing, and alerting must be deployed. Using the NetApp FPolicy capability with the partner ecosystem, UBA can be used to alert suspicious or aberrant data access that is out of the normal pattern and, if necessary, take actions to deny access. FPolicy partners are moving beyond UBA toward machine learning (ML) and artificial intelligence (AI) for greater event fidelity and fewer, if any, false positives. All events should be logged to a syslog server or to a security information and event management (SIEM) system, which can also employ ML and AI. Refer to the FPolicy Architecture diagram for details on this workflow.
ONTAP and FPolicy as Your MCAP Segmentation Gateway
In its original concept, Zero Trust was envisioned to use a segmentation gateway to protect the MCAP. To protect a data MCAP, you can create a Zero Trust solution by using all the strong capabilities in ONTAP as well as FPolicy and the FPolicy partner ecosystem as the segmentation gateway. The ONTAP Zero Trust model also provides a powerful compliance framework for many industry requirements.
The threat landscape—both internal and external—continues to be an increasing challenge for organizations to protect their data. NetApp ONTAP and the FPolicy partner ecosystem will continue to help you meet these new challenges by advancing the capabilities you can rely on, including advanced technologies and techniques such as artificial intelligence, machine learning, and deep learning within the Zero Trust model.
For more detailed information, refer to the following resources:
Daniel Tulledge
Dan is a Senior Technical Marketing Engineer for ONTAP Security for nearly two years at NetApp. He has focused on all aspects ONTAP hardening including encryption in flight and at rest, multifactor authentication, as well as addressing compliance issues with ONTAP such as requirements for the Payment Card Industry or the EU General Data Protection Regulation. He has thirty plus years of experience in the networking and security technology industry. Most recently, Dan worked for Cisco Systems Inc. for 17 years in senior technical marketing, product development, services operations architecture positions spanning a large breadth of Cisco technologies with emphasis on product security features, cyber security and trustworthy systems. Prior to Cisco, he worked at AlliedSignal, IBM, and CA.


